3. THE PRODUCTS OF PT SYDECO
$ 1. ARCHANGEL, the intelligent firewall
What is ARCHANGEL?
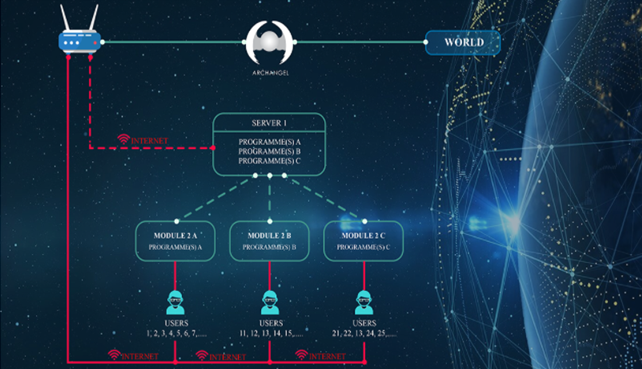
Archangel is a smart Box that creates an internal network within a company or an office and through which all data transmitted via the internet, either via WIFI or cable, must pass. It does also exist as a program.
ARCHANGEL Features :
ARCHANGEL© is equipped with:
3 FIREWALLS,
4 INTELLIGENT AGENTS,
2 BRAINS,
HONEY POT
DINAMYC ROUTER and
2 SWITCHS.
In order to filter all the flows entering in an Office and to protect all its installations which are connected through VPN including IoT against any external attack and against any lateral contamination.
ARCHANGEL Function
Its function is to protect all computers or other mobile devices belonging to this network against any cyber-attack from outside and to protect each computer belonging to this network against the spread of a virus or a worm from an infected computer to another computer on the network.
Operating System of ARCHANGEL
1. ARCHANGEL© is using its own Operating System built by SYDECO: ArchanOS Michael 18.2
2. The Operating System used by ARCHANGEL© has been created by PT SYDECO. It is an original Operating System.
3. It can be described as being a Multi-tasking, Multi-user, Embedded and Real-time Operating System.
4. It belongs to the category of MONOLITHIC KERNELS.
Different options
I - The ONE WAY SYSTEM (ARCHANGEL OW)
That allows only one-way traffic to be used, which is very useful for securing an industrial network for example to permit a one way access and forbidden the access
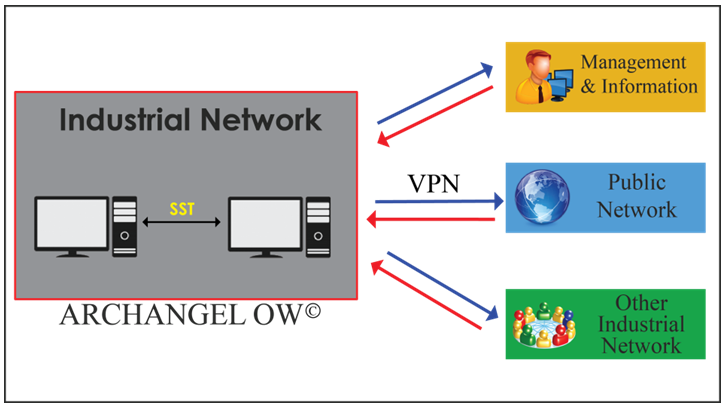
Figure 5: Archangel One-way
II – With INTELLIGENT AGENT 4 (ARCHANGEL A4)
Archangel A4 has a fourth intelligent agent whose function is to stop the takeover of the operational system by an external agent and its automatic replacement by the original version.
III – The ONE WAY SYSTEM with INTELLIGENT AGENT 4
For example to protect the backup center of a financial company
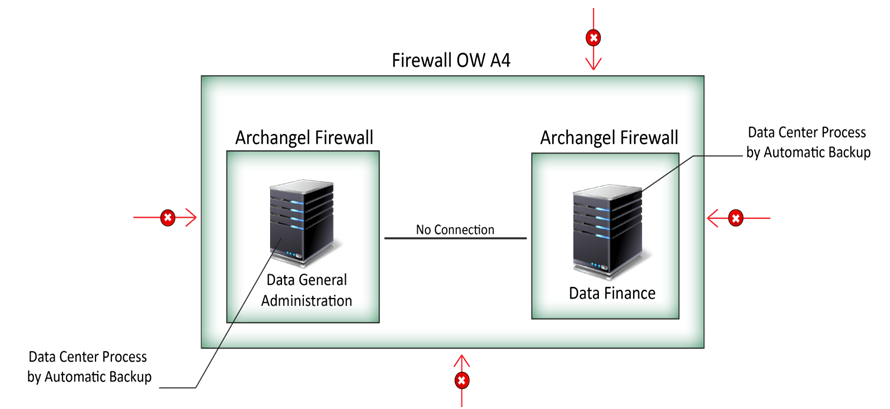
Figure 6: Archangel One-Way using Agent 4
$ 2. ARCHANGEL PLUS
ARCHANGEL USING RADIO WAVES FOR TRANSFERRING
DATA AND VOICE CALLS
In order to protect the equipment that is connected or not to internet and to protect the transfer of data and calls even where internet is not accessible, PT SYDECO has created ARCHANGEL PLUS.
ARCHANGEL© with its own Operating System, ArchanOs Michael 18.2, is a mini computer that does already integrate SST© (Secure System of Transmission), another product of PT SYDECO. It protects the devices and data at rest and during their transfer between 2 ARCHANGEL© that are connected by VPN.
ARCHANGEL PLUS also integrates tools that allow sending to another ARCHANGEL PLUS data and calls protected by SST© using Radio Waves inside a VPN. SST© is used for Server SMS.
$ 3. SydeCloud, the secure online file sharing
Sydecloud is a service for securely storing and sharing files. SydeCloud’s Server is located on the customer's premises protected by ARCHANGEL.
DATA is stored and conveyed protected by the encryption system of SST. When conveyed, DATA are protected by VPN created by ARCHANGEL which is on the user’s premises. Because SST Server is also on the user premises, there is no third party involved: Nobody can interfere and disrupt the service.
$ 4. SST, the encryption system
SST© (Secure System of Transmission) is a revolutionary system of protection of data, of whatever nature, by their translation into an unknown language created by a brain and written in the form of waves, a language which we call ALIEN and which knows no written character.
SST© is based on Artificial Intelligence, Unlike existing systems that protect data by encryption, SST© DOES NOT USE ANY KEYS.
SST©:
- Protects all data,
- Protects all passwords,
- Can seal all transaction,
- When used for a messaging service, makes it E2E,
- Protects the content of telephone conversations or video calls in the same way.
SST© IS THE MOST IMPORTANT ELEMENT OF A WELL THOUGHT-OUT
CYBER-SECURITY
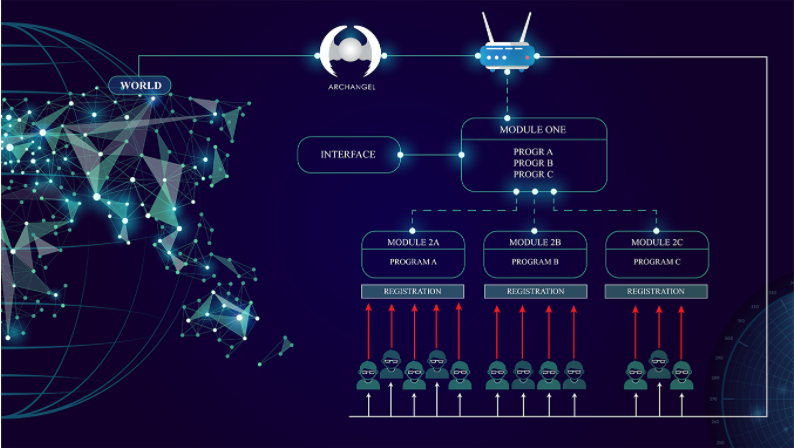
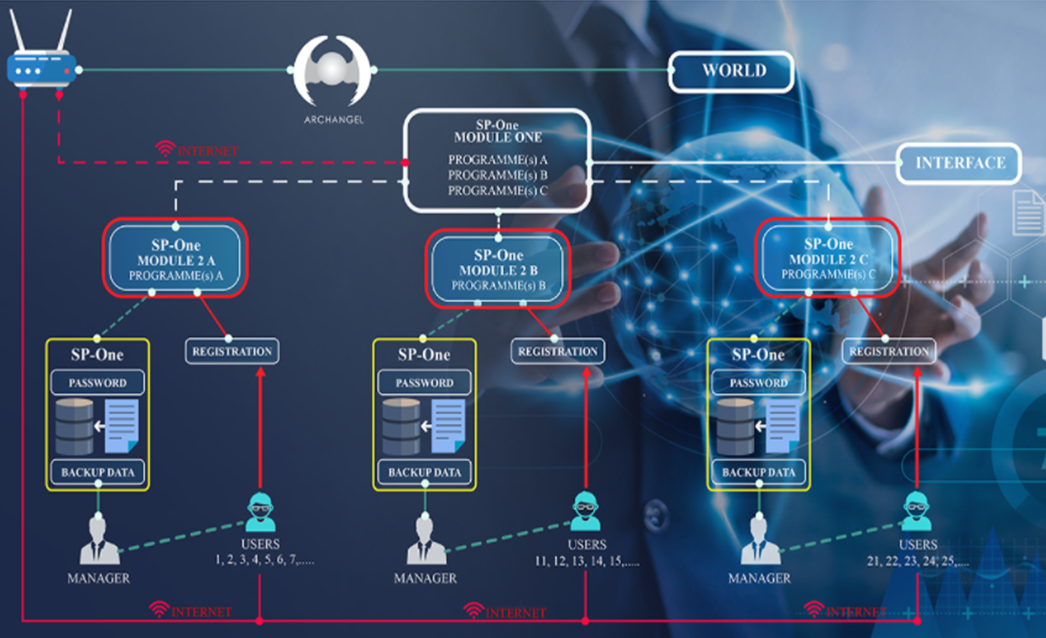
$ 5. SP-One, Source Code and Program Protection
SP-One© is a program and a system that is creating hermetic secure shelter around the source code or programs that you are using either in your office, administration, at University, in your Cloud, in any mechanic and in SaaS.
SP-One© thanks to its method allows you to work with your programs even when such programs are hosted in a hermetic shelter
Benefits of SP-One
One of the most important benefits of SP-One© is that even if you are victim of a Ransomware and during and after such attack, THERE WILL BE
NO DISCONTINUITY, in your work, your production, and your services:
1. The Hospital will continue to care,
2. The Industry will continue to produce,
3. The University will continue to educate their students,
4. The Public Services will not stop.
NO HUMAN LIFE IN DANGER, NO RANSOM TO BE PAID, and NO LOST IN PRODUCTION, NO LOST TIME IN REPAIRING THE SYSTEMS…
What SP-One is made for?
1. Protecting program from piracy,
2. Protecting program from damage,
3. Making sure that the programs keep running,
4. Allowing a scheduled automatic backup system,
5. Giving a warning when there is an attempt of non-authorized login or penetration in the system
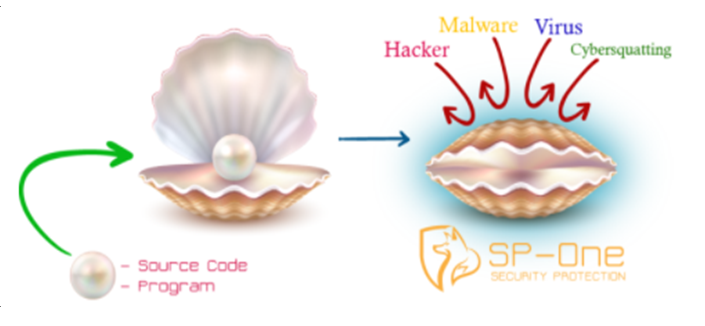
Figure 7: SP-One protects Programs and Source Codes against any kind of attacks
$ 6. SydeChat, the Secure Messenger Service
SydeChat is a mobile application that allows its user to:
- Give and receive calls,
- Give and received Vide Calls,
- Organize Video conference even with more than 10 participants,
- Create groups and organize virtual meeting with more than 10 persons who can interact with each other,
- Work in real time on the same document with several colleagues that you can see and talk to,
- Easily import all contacts from your old messenger service.
Characteristics
- all conversation are secured e2e,
- all communication of documents are secured e2e,
- all video conference are secure e2e,
- all remote working meetings are secured e2e.
The Security and confidentiality of the Data at rest or in motion is provided by the revolutionary encryption system of SST© that is not using any key and by the fact that all data in motion is conveyed inside VPN itself protected by SST©
Sydeco’s SERVERS, PROGRAMS, DATABASE, BACKUPS are protected by the ALL-IN-ONE IT SECURITY SOLUTION, where ARCHANGEL, SST and SP-One are implemented into a ZERO TRUST ARCHITECTURE (ZTA).
There is NO INTERRUPTION in the service even when the servers are under attack.
Available Options
It is possible for the user to:
- keep his data (history) in his phone where they are protected by SST©,
- Keep his messages & data secured in Sydeco’s cloud, nothing, no trace in his phone,
- Keep his messages & data secured in his own computer, protected by ARCHANGEL-SST, nothing, no trace in your mobile phone or,
- Create his own messenger service by Installing, in his own server, SydeChat which is protected by ARCHANGEL-SST and SP-One. So the user has is private chat and his data & messages are kept in his servers. There is nothing, no trace in his mobile phone and no one can access his chat unless they are a member of the user’s network.
IV – CONCLUSIONS
PT SYDECO has created a comprehensive security system based on epidemiological methods that includes a ZERO TRUST architecture and the most powerful tools from the latest technologies to protect against the disastrous consequences of Ransomware and other attacks.
The ALL-IN-ONE system of PT SYDECO offers a real-time response and follows the 0-0-0 rule:
- Zero minute to notice a threat,
- Zero minute to understand it and,
- Zero minute to react.
ALL-IN-ONE of PT SYDECO is the best solution on the market for IT security.